Update (2024)
Modern browsers don't run Java applets any more. Many other improvements have been made in Mac and browser security. This specific thread has faded, but there are new security attacks. Stay vigilant.
The Problem
(04/07/12) A serious security threat, a new variant of the Flashback malware, was noticed in April 2012. It attacks Macs that just visit an infected web page. It can infect your computer even if you do not input your password. The malware tries to steal financial passwords from your computer. It has been estimated that over 500,000 Macs have been infected.
What kind of web sites could get you in trouble? This time, it wasn't just porn sites: just reading blogs could trigger the attack. According to Kaspersky Labs, many thousands of WordPress blogs were compormised by an infected server plug-in that could infect Macs as well as PCs.
Flashback's main method of attacking Macs at this time was via Java. Other versions of Flashback, and other malware, exploit other weaknesses in web browsers, including Flash and JavaScript. It is still out there and mutating to try to exploit new holes.
Preventing Infection
(2017) The instructions below are for OS X 10.6 through 10.8. If you are running a more recent version of OS X, they won't apply. The safest thing to do currently is to disable your computer's ability to run Java applets in the browser, and in fact this has become the default. Also, Apple no longer distributes Java: the latest version is available from Oracle, if you need it.
(04/07/12)
The ![]() Intego Security Blog described this attack.
The solution was to protect your computer by installing an update for Java that Apple released on 04/03/12,
using > to install it.
It is usually a good idea to install security related updates from Apple .. I wait a few days and check MacInTouch to make sure others are not having problems.
These updates are usually only available if you are running the most current versions of OS X, either 10.6.8 or 10.8.x:
another reason to keep up to date.
Intego Security Blog described this attack.
The solution was to protect your computer by installing an update for Java that Apple released on 04/03/12,
using > to install it.
It is usually a good idea to install security related updates from Apple .. I wait a few days and check MacInTouch to make sure others are not having problems.
These updates are usually only available if you are running the most current versions of OS X, either 10.6.8 or 10.8.x:
another reason to keep up to date.
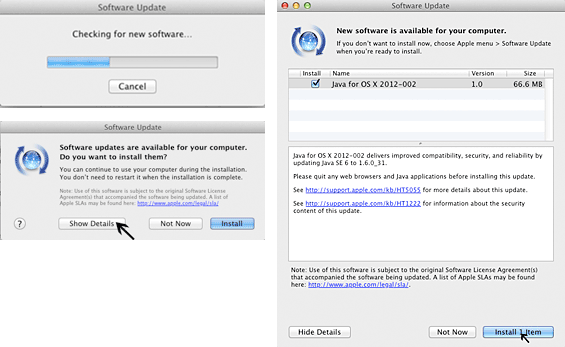
(When you update your computer, also make sure your browsers, Flash and Word are up-to-date: there continue to be attacks on Macs using these packages.)
Many commentators complained that this fix came out too slowly. The Java vulnerability was known to Oracle in October 2011; they released a patch on February 14 2012. Apple was testing a Mac OS X upgrade for Java in mid-February. A version of Flashback that exploited the hole on Macs was observed in the wild at the beginning of March. Anti-virus productslearned to detect the Mac exploit in early April, and Apple released its update a few days later. Apple later (13 Apr 2012) released additional updates that disinfect your computer if it has been infected.
If You Cannot Install the Upgrade
If you are running a version of OS X prior to 10.6, the Java upgrade will not be available to you until you upgrade your OS. If you have a PowerPC Mac, it can't run a version of OS X that has a security upgrade. In these cases, the best things for you to do are:
- Limit your Web surfing to trustworthy sites. (Of course this is very hard: how would you know how a given web site is secured?)
-
Disable Java applets in your browsers (this may break some web sites):
- Safari: : uncheck
- Firefox: : disable
- Chrome: : click
- Disable Java on your computer entirely. (This may break some applications.)
Other Things You Can Do to Reduce Risk
I do all of these.
- Keep your browsers and the plugins they invoke up to date.
- Don't click on links in mail messages unless you are sure that the message is not forged and the link goes where it says it does, and the target site is trustworthy.
- Use Firefox or Chrome instead of Safari.
- Install the NoScript or ScriptNo plugin, and configure it to allow only sites you trust to send Javascript.
- Buy and install Little Snitch, and configure it to allow your applications to contact trusted remote sites.
Anti-virus
The Mac anti-virus packages from Intego, F-Secure, Kaspersky, and many others, claim to detect and block this malware. (Subscriptions cost money, about $50/year/computer.) Anti-virus products are all about locking the barn door after someone's horse has been stolen. They reduce risk but don't eliminate it; they cannot block malware variants that have not been discovered yet. If you use them, you have to hope that future Mac malware will be noticed, and updates sent out to your computer, before you get infected. I have not tried any Mac anti-virus package yet, except the free ClamXAV malware scanner, which works OK.
Is Your Computer Already Infected?
If you got an unexpected request for your password while browsing some random web site, that's a bad sign.
You can check if your computer has extra libraries loaded when applications are run, which is a mechanism used by the malware. The instructions are from the F-Secure blog. To make sure your computer is OK, do this. Copy the following four lines into the clipboard:
defaults read /Applications/Safari.app/Contents/Info LSEnvironment defaults read /Applications/Firefox.app/Contents/Info LSEnvironment defaults read /Applications/Chrome.app/Contents/Info LSEnvironment defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
In the Finder, open the Applications folder, open the Utilities folder inside it, launch the Terminal application. Paste the 4 lines. You should see:
MACHINE:~ USER$ defaults read /Applications/Safari.app/Contents/Info LSEnvironment 2012-04-07 18:42:31.865 defaults[26110:903] The domain/default pair of (/Applications/Safari.app/Contents/Info, LSEnvironment) does not exist MACHINE:~ USER$ defaults read /Applications/Firefox.app/Contents/Info LSEnvironment 2012-04-07 18:42:31.921 defaults[26111:903] The domain/default pair of (/Applications/Firefox.app/Contents/Info, LSEnvironment) does not exist MACHINE:~ USER$ defaults read /Applications/Chrome.app/Contents/Info LSEnvironment 2012-04-07 18:42:31.945 defaults[26112:903] The domain/default pair of (/Applications/Chrome.app/Contents/Info, LSEnvironment) does not exist MACHINE:~ USER$ defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES 2012-04-07 18:42:44.530 defaults[26113:903] The domain/default pair of (/Users/thvv/.MacOSX/environment, DYLD_INSERT_LIBRARIES) does not exist
The numbers will be different, of course. But you want four "does not exist" messages. If you see something else, then your computer may be infected. The Apple update removes the infection if it is found.
Understand that the malware writers are constantly trying new tricks, and that they will change their malware to evade detection and removal.
How Flashback Works
- You navigate to an infected web page. Many Wordpress and Joomla blogs were infected starting in March 2012.
-
The infection page executes some Javascript code that redirects to a script that tries several ways to infect your computer.
It may put up an installer dialogue asking for your password, and only use the Java approach if you refuse.
In any case, eventually the infection page loads a malicious Java applet.
Normally applets can't write on disk or modify defaults;
the malicious applets make calls that raise its privileges so that it can
- fetch additional infection code and install a "back door" facility
- write the infection code to disk, using names that will be hidden, in places you won't look
- modify directories and files to cause the malware to be launched
- modify application settings so that malicious libraries will be loaded the next time you start applications (these are the LSEnvironment and DYLD_INSERT_LIBRARIES values above)
- modify system software to not show the existence of the virus
-
When you start a browser, the bad guys' code runs instead of the real code. It can
- read any web page you view, and send the information to a bad-guy server
- change any web page you view, to hide things it did, or insert ads or false information
- read any file on your computer and send its contents to the bad guys
- write files on your computer to destroy your data, or update or install further malware
- update system software to prevent you from removing the malware or backing up your files
- fetch more malware to do further nasty tricks
- There is little information about what the bad guys do with the information they steal. Your online credentials might be sold to others and not exploited for some time.
- (Strictly speaking, this malware is not a "virus," since your computer is not used as a means of infecting other computers. It's not really a "Trojan Horse" since it is not hidden in a document you open expecting one thing and getting attacked instead... unless you count the web page or mail message that inserts the infection. I am just calling it "malware.")

